Aruba's OS-CX switches have the ability to profile devices connected to ports and dynamically assign roles and policies (ACLs) to those ports. The ACLs can include the usual stuff--filtering on source, destination and protocol. But, they can also include configuration parameters like VLAN assignment.
Here's a simple example that can be useful when deploying access points with bridged VLANs. In this example, the switch makes a profile of the connected device using LLDP (you can use CDP, too), parses the response and assigns a role to the port. The role has policies that assign VLANs.
To see how this would work, let’s say that we have an access point on port 1/1/10. Examining the LLDP query on the port, we get the following:
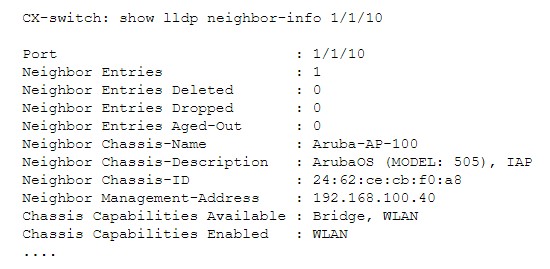
In our test for the presence of an AP, we will search the description for "IAP". To make the example a little more interesting, we will also skip any AP-305s we might find. The following are rules that will match our LLDP port access test. These are arranged like a sieve; the first pattern that matches wins.
port-access lldp-group AP-lldp-group
seq 10 ignore sys-desc 305
seq 20 match sys-desc IAP
Next, we define the role and the policies that we want to associate with access points that match the above port-access tests. The block below says that the role is called "lldp-AP," and that the policies "create a trunk and allow VLANs 12,22,40 and 100, and make 100 be the native VLAN."
port-access role lldp-AP
vlan trunk native 100
vlan trunk allowed 12,22,40,100
This last section is the glue that pulls the port-access tests and the role assignment together. It says "if the device on port x matches AP-lldp-group tests then assign the role of lldp-AP."
port-access device-profile AP-lldp-devprofile
enable
associate role lldp-AP
associate lldp-group AP-lldp-group
Dynamic profiling can be applied to other kinds of devices too, including printers, projectors and phones. When used in conjunction with Aruba Central or NetEdit, elements of the policies and port-access tests can be described using variables, such as this:
port-access role lldp-AP
vlan trunk native %_native_VLAN%
vlan trunk allowed
%_wireless_VLANs%,%_native_VLAN%
When used in conjunction with ClearPass and controllers, the ports can implement enhanced profiling, role assignment and dynamic segmentation whereby VLANs that don’t even exist on the switch can be tunneled from other parts of the organization.